In this day of never-ending new technology, there is an enemy lurking. It’s a sneaky enemy that preys on our fears. In the end it can be your interminable nightmare. I’m talking about computer viruses and, specifically, fake antiviruses or Fake AVs.
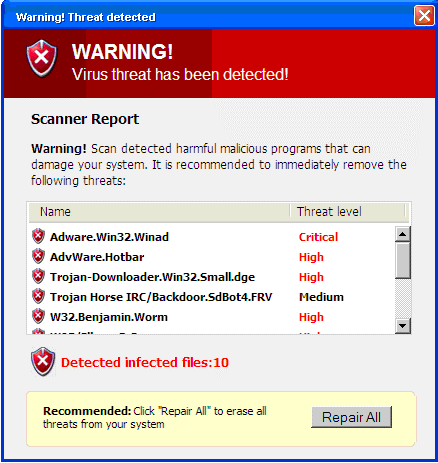
When you boot up your personal computer, you have the self-assurance of that icon next to the clock that says your you have antivirus software installed. (At least I hope you have antivirus software installed.) Then you open your browser of choice and start to navigate the Internet and encounter a message like this:
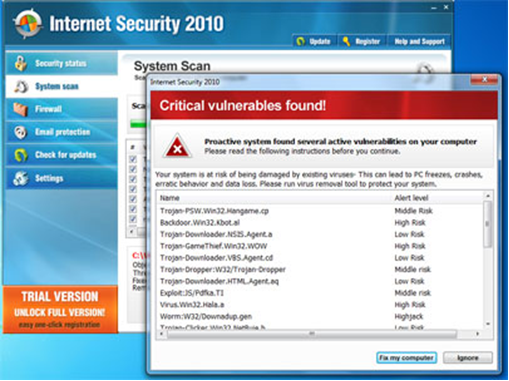
You start to panic! How can this be? My antivirus software is up-to-date! The next thing you do is you click the “Repair All” button. Then you see the following:
You start to feel better because you have the application before you that will take care of it. You then notice that in order to completely fix your machine, you need to order the “Full Version” instead of the “Trial Version” that has just diagnosed your computer. At this point many people will abort or try to abort. Uh oh! You click on the “x” and nothing happens! The feeling of trepidation starts to take over. What has just happened and how do you fix it?
I have witnessed this is a scenario several times. Fake AVs come in many shapes, forms and titles. The banners look real. The icon that has now taken over your machine looks real.
What is the motive of this offender? It’s twofold. First, they want your credit card information. Many users will quickly “upgrade” to the full version thinking that is the only way to dispel what is before them. The scam artists usually ask for a one-time fee ranging from $50 to $200 in some cases. After the transaction is made, they have your credit card information and you are stuck with a zombie-like machine that will not respond to the simplest requests.
I mentioned that this crime is twofold. After your machine is infected, the fraudulent hackers have the ability to use your machine for the emergence of their viral army. If you leave the fake software on your machine for a long period of time the hacker can access any file, any time.
Fake antiviruses are around every corner. They can reside on legitimate websites. They certainly hang out on popular sites such as Facebook, MySpace, and YouTube. They can easily be executed on file sharing sites.
How do I combat this? Unfortunately there are so many degrees of infection, no one fix can fix all. I write this article as a warning. If you ever see a pop-up like the first illustrated picture, your best way to avoid infection is to not click on anything. If you click on the “x,” it’s usually programmed as “enter.” In fact, any click can start the install process.
Your best weapon at this point is the task manager on a PC, or the activity monitor on a Mac. End your browser service! If you stop this service immediately you will escape any type of installation. If you can’t find your running browser service, reboot your machine. As long as no clicks were made, the installation should be avoided.
Unfortunately, real antivirus will not stop these types of pop-ups. Preemptive measures you could take are running an anti-spy software. This may help you if you are infected, but it will not stop a potential installation. If you do get infected consult a computer technician professional as soon as possible. It may be possible to delete the fake antivirus but the process can be long, intensive, and sometimes unsuccessful. Many machines end up being reformatted to cure this!
Let this article be a warning of what to watch for. When in doubt, don’t believe it. Abort!




 Create professional development programs that help REALTORS® strengthen their businesses.
Create professional development programs that help REALTORS® strengthen their businesses.
 Protect private property rights and promote the value of REALTORS®.
Protect private property rights and promote the value of REALTORS®.
 Advance ethics enforcement programs that increase REALTOR® professionalism.
Advance ethics enforcement programs that increase REALTOR® professionalism.
 Protect REALTORS® by providing legal guidance and education.
Protect REALTORS® by providing legal guidance and education. Stay current on industry issues with daily news from Illinois REALTORS®, network with other professionals, attend a seminar, and keep up with industry trends through events throughout the year.
Stay current on industry issues with daily news from Illinois REALTORS®, network with other professionals, attend a seminar, and keep up with industry trends through events throughout the year.